Building Cyber Resilience Within the Evolving Global Supply Chain
Cyber ResilienceArticleJanuary 14, 2026
Considerations of Today’s Supply Chain
Today’s supply chains are engineered to seamlessly manage the flow of goods, information, and resources across borders—meeting consumer demand while enhancing business operations. The value of this interconnectedness lies in optimizing production costs, improving product availability, fostering global trade, and fueling economic growth by connecting markets and leveraging comparative advantages.
However, these impressive benefits also come with significant challenges: rising costs, labor shortages and disruptions, political uncertainty, and above all, escalating cyber risks.
To address some of these obstacles, many organizations are exploring onshoring, nearshoring, and friendshoring strategies. The U.S. Department of Homeland Security contextualizes the current landscape: “The world is at a crossroads whether to continue to focus on onshoring or improving the resilience of global supply chains.” No matter the approach, organizations working with third-party vendors must regularly re-evaluate their supply chain and conduct thorough cybersecurity reviews—both internally and externally—to mitigate potential negative impacts.
Breaking Down the Cyber Risks
Any disruption in the supply chain—particularly vendor changes due to shifts in sourcing strategy—can increase cyber exposure for all involved. In response to these challenges, 60% of businesses aim to develop alternative suppliers, 42% focus on improving business continuity initiatives, and 37% work to identify and resolve supply chain bottlenecks.
Every new supplier adds a potential cyber risk, especially if the partner has not established a proven security record or has not been thoroughly vetted for cyber maturity. The risks are tangible: nearly 75% of third-party vendor data breaches specifically target the technology and software segments of the supply chain, and 29% of all data breaches are attributed to third-party attacks (DHS study).
While re-routing supply chains might address some risks at an international level, it can just as easily create similar risks on a smaller, regional scale.
Cyber and Business Resilience Responses
Organizational leaders consistently rate cyber incidents and business interruption as their biggest risks—risks that are only intensified by ongoing supply chain challenges. To be resilient, businesses in every sector should establish multi-layered defenses that prioritize both business continuity and robust cybersecurity. While no company welcomes a supply chain-related cyberattack, preparation for such events is essential.
Incident Response (IR) Preparation
There is no single solution for complex systems like the supply chain, but there are practical steps that make a real difference. Effective response to cyber or continuity threats requires advance planning. A strong IR framework ensures leaders at every level know their roles if a cyber incident occurs. In the context of supply chains, IR planning means identifying contingency measures to minimize damage, reduce downtime, improve decision-making, and enhance communication during periods of stress.
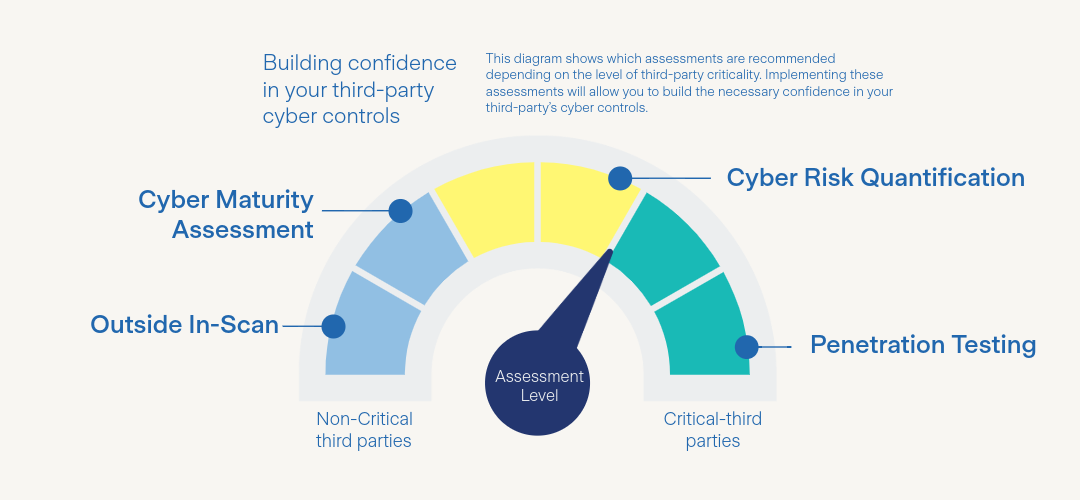
Cyber Assessments
Both primary organizations and their third parties benefit from regular cyber assessments.
- Cyber Risk Quantification helps identify at-risk assets and assesses the financial implications of potential incidents, enabling smarter investment in security.
- Cyber Maturity Assessments for vendors mean risks are caught and remediated early, before threat actors can take advantage.
Every endpoint should be evaluated to limit unauthorized access. For non-critical vendors, a health check—a lightweight review of people, processes, and technology—is often enough. Critical third parties should undergo penetration testing to expose potential vulnerabilities. Confidence in your third-party cyber controls brings not only security but also peace of mind.
Security Operations Center (SOC) Monitoring
Third-party vendors are only one element of supply chain risk. It’s equally vital for organizations to maintain robust internal controls and security programs. Managed Detection and Response (MDR) solutions, monitored 24/7/365 by a dedicated SOC, are among the most effective cyber strategies—ensuring threats are detected and remediated swiftly.
Managing daily business operations is demanding. Partnering with experienced cyber professionals allows leaders to focus on their core business, knowing their operations are protected by skilled, watchful eyes.
Considerations for Manufacturing and Construction
Discussions about onshoring, nearshoring, or friendshoring frequently focus on manufacturing and construction, emphasizing local resources and labor. For construction organizations, these shifts help minimize delays and provide greater control over risk management and resilience practices.
Manufacturing is considered a critical industry for most economies—making it a prime target for both financially motivated threat actors and political adversaries. The FBI reports that manufacturing is the second most-targeted industry for ransomware. National initiatives like the CHIPS Act, aiming to boost domestic semiconductor production, highlight just how significant these supply chain shifts can be for global security and stability.
Meanwhile, U.S. construction—particularly in manufacturing facilities and urban development—is booming, with MIT research indicating a 40% increase in recent years. As investment grows, so do cyber risks: 59% of construction firms experienced a cybersecurity threat in the past two years. Heavy reliance on third-party vendors amplifies the potential for disruption.
Tody’s supply chain landscape brings both remarkable opportunity and substantial challenges. As organizations navigate the complexities of the global market, they must remain vigilant against the cyber risks accompanying supply chain disruption and vendor change. The shift toward onshoring, nearshoring, and friendshoring only highlights the need for robust cyber resilience and thoughtful vendor assessments.
By implementing a comprehensive cybersecurity program, businesses—especially in critical industries like manufacturing and construction—can strengthen their defenses, protect continuity, and build long-term trust. Purposeful efforts to enhance cybersecurity help mitigate risk and foster a secure, sustainable business environment for the future.
Sources
- DHS: Building Supply Chain Resilience
- Allianz Risk Barometer
- FBI: 2023 IC3 Report
- MIT: Reshoring Renaissance
- Dodge Construction Network
- Zurich Cyber Supply Chain Factsheet
